Ubuntu server 14.04 LTS does not get security updates to the ARM repository. Despite LTS standing for Long Term Support. Something that I did not expect.
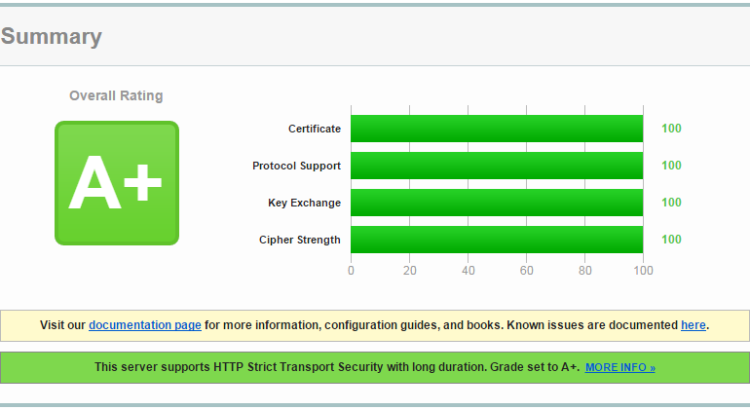
When running webservers with SSL HTTPS on the Odroid-XU, it is vulnerable to several security issues, such as the POODLE and CCS Injection Vulnerability (CVE-2014-0224). This is solved in more recent versions of OpenSSL, but those are not available from the ARM repositories. To solve this OpenSSL can be build from source. CVE2014-0224 is solved from OpenSSL 1.0.1h, and POODLE from 1.0.1j. Generally it is best to install the most recent version of OpenSSL. The following steps describe how to get the job done. This is assuming the build is performed as the root user. Otherwise sudo may need to be added before the make install and cp and ln commands:
#update openssl to fix various SSL vulnerabilities
wget https://www.openssl.org/source/openssl-1.0.1m.tar.gz
tar xzvf openssl-1.0.1m.tar.gz
cd openssl-1.0.1m
./config --prefix=/usr/ --openssldir=/etc/ssl shared
make #make -j5 fails!
make install
cp -a /lib/arm-linux-gnueabihf/libssl.so.1.0.0 /lib/arm-linux-gnueabihf/libssl.so.1.0.0.backup
cp -a /lib/arm-linux-gnueabihf/libcrypto.so.1.0.0 /lib/arm-linux-gnueabihf/libcrypto.so.1.0.0.backup
ln -sf /usr/lib/libssl.so.1.0.0 /lib/arm-linux-gnueabihf/libssl.so.1.0.0
ln -sf /usr/lib/libcrypto.so.1.0.0 /lib/arm-linux-gnueabihf/libcrypto.so.1.0.0
Then to check whether the build succeeded, extended version information can be retrieved. Read More